Bad Error Messages
Last week I was trying to log into an application and I noticed a few problems with error messages divulging information that could be of use to an attacker. I think that the problems are that I think we would do well to avoid in our development.
I couldn't remember my password so was trying a few of the likely suspects. When entering my NTID and a guess at the password I got the following error message:
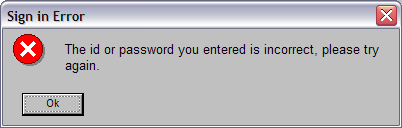
This error message is good (from a security standpoint). It doesn't disclose whether or not it is the username or the password that is wrong. No additional information is provided to an attacker. Next I thought that the problem may be that the application uses employee ID so I tried again with my employee ID which resulted in the following error:
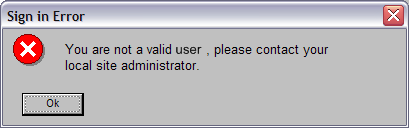
This is a problem, as it tells me (and could tell an attacker) that my NTID is a valid ID. This other error message also discloses more information about the password if you enter a password that is too long or short.
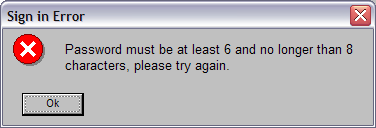
Assuming the visible ASCII characters as the search space there will be 6,094,999,515,629,760 valid passwords. That is still a lot for a brute force attack. But restricting to alphabet characters and then just lowercase drops that number considerably (53,439,957,921,792 valid passwords and 208,518,148,800 valid passwords respectively). Furthermore, I bet that a dictionary attack of common 6-8 letter passwords would be able to get into a lot of accounts.
By itself, I don't think this is a big problem. Any of these attacks could easily be detected with good logging and even the smaller search space of a dictionary attack could easily be made intractable by throttling login requests.
One common countermeasure that introduces more problems than it solves is locking out accounts after a certain number of failed login attempts. Locking accounts is an idea that seems good, but opens another attack vector. Specifically, automated account blocking makes for a really, really easy Denial of Service attack.
Still, I think it is important to remain aware of the information we disclose in error messages. You don't want to help an attacker out.
The proper and more secure practice is for all three of these error conditions to use the first, generic error message and perhaps include a “trouble logging in” link to improve usability. These problem fall under the heading of Improper Error Handling. More information can be found via OWASP (the Open Web Application Security Project)
More Articles on Software & Product Development
- Agile With a Lowercase “a”
- ”Agile“ is an adjective. It is not a noun. It isn’t something you do, it is something you are.
- How Do You End Up With A Great Product A Year From Now?
- Nail the next two weeks. 26 times in a row.
- Build it Twice
- Resist the urge to abstract until you've learned what is general to a class of problems and what is specific to each problem.